The world of the computer hacker can seem as alien as Sanskrit or quantum physics. But it’s worth trying to understand the geniuses behind the internet as well as the mindset of the minority of hackers who turn bad. Who knows, perhaps you’ll discover your inner geek?
What is a hacker?
Let’s clarify some terms. Geeks are knowledgeable and obsessed enthusiasts (not necessarily about computers). Hackers, in the true sense, are computer experts. See the Wikipedia definition of ‘hacker.’ All hackers are geeks, but not all geeks are hackers.
Hackers prefer to describe their brethren who have gone over to the dark side as crackers or black hats. This site prefers to differentiate between good and bad hackers by context because the word cracker isn’t widely understood. In short, not all hackers are evil.
Good hackers and bad hackers
Hackers are the architects of the modern age. The hacker ethic is collaborative, meritocratic, idealistic and fundamentally humanistic.
Among its products are the internet, the Linux operating system, computer games and the Worldwide Web.
How to be a good hacker
Here are some of the characteristics exhibited by good hackers:
- Know how to program computers, usually in several different languages.
- They respect: problem-solving, elegant solutions, creativity.
- They don’t respect: suits, attitude without competence, bureaucracy.
- Enjoy reading computer manuals and finding out how things work.
- Motivated by kudos and the challenge.
- Concentration, persistence, playfulness, abstraction.
- Absorb, retain and use large amounts of detailed information.
- Often widely but eclectically well-read.
- Enjoy wordplay and puns.
- Love science fiction. True adepts read Stanislaw Lem.
- Love Star Trek, Star Wars (but not Jar Jar Binks), Lord of the Rings, Dilbert.
- The influence of Zen Buddhism.
- Contribute to an open-source software project and/or publishes useful information.
“The hacker culture doesn’t have leaders, exactly, but it does have culture heroes and tribal elders and historians and spokespeople.’ –Eric Steven Raymond in his article, How to become a hacker.
Geek grammar
Once you’ve got the attitude, you need to learn the language. Here are a few grammatical rules and some basic vocabulary to get you started.
Hackers speak a dialect of English but with some characteristics variations:
- Verb doubling at the end of a sentence to add emphasis. ‘The disk heads just crashed. Lose, lose.’
- Sound-alike slang punning on a well-known proper noun.
- Overgeneralisation. Playing with language to turn nouns into verbs, superlatives or to poke fun. For example: obviosity, winnage, hakification, disgustitude, marketoid.
- Spoken inarticulations. Geeks actually say ‘mumble’ and ‘sigh.’ They are audible smileys.
- Anthropormorphisation. ‘My computer couldn’t cope with all the stress and crashed.’
- Comparatives. For example, the spectrum of: ‘Broken-flaky-dodgy-fragile-brittle-solid-robust-bulletproof-armor-plated’ or ‘crock-kluge-hack-win-feature-elegance-perfection’.

Hacker vocab
Two useful dictionaries are The Hacker Dictionary and The New Hacker’s Dictionary, which are primary sources for this article. Here are a few useful terms to get you started:
- ASCII (American Standard Code for Information Interchange) a widely used code for digitally representing letters, numbers and punctuation marks.
- Back door. A security hole that has been deliberately including in a piece of computer software by the author. See Die Hard 4.
- Bug. An error in a computer program.
- Cracker. A hacker who does bad things. Also known as a black-hat hacker.
- Delta. The difference between two amounts (‘the delta was 30 percent’) or the differences between two files.
- Dumpster diving. Searching through rubbish to find revealing private information.
- Easter egg. An unexpected ‘feature’ built into a computer program by the author.
- FAQ. Frequently Asked Questions.
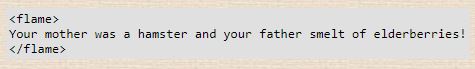
- Flame. An irate email.
Hello world!
- Hello world. The first output from the first program. But the last output is occasionally, ‘I’m sorry Dave, I can’t let you do that.’
- Kluge (or Kludge). An effective but inelegant solution to a problem.
- Moby. Big, as in Melville’s whale.
- Nontrivial. Difficult, as in ‘that was a nontrivial kluge.’
- Open-source. Computer software that has been developed in a collaborative way by volunteers on a non-commercial basis.
- Owned. When bad hackers take over a computer.
- Ping. A simple program that communicates with another computer over a network to see if it is responsive. Also, now often used as a form of human communication (‘I’ll ping you later’).
- Script kiddie. A wannabe hacker who uses widely available tools without real understanding.
- Spacewar! The first computer game. Written by true hackers at MIT in 1963.
- Wizard. A hacker of great ability. It also can describe a high level administrator on a multi-user adventure game.
- XYZZY. The magic word in Adventure, a game from 1977; often used in other programs.

Punctuation
- !{insert word} – Not or no-. As in ‘!good’ meaning bad.
- / or <> – Not equal, or not. As in ‘its/it’s.’
- <{insert word}> – Used to bracket a phrase with extra, contextual information. The format is derived from the code underlying webpages where typographical and layout information is enclosed.
- Some members of the community use l33t speak: numbers and punctuation to substitute for letters. For example, 0wn3d = owned (i.e. compromised or hacked).
- Another trick is to add a ‘z’ to a word to make a plural, often with subversive connotation. For example, warez (‘wares’) means pirated software. See here for more on hacker punctuation.
Where next?
- 21 sure signs you’re a geek on this blog
- Forever Geek which includes the invaluable guide to making your own Jedi robes.
- Use the Geek Code to specify your exact status as a geek.
- Take the Geek Test. (I scored 46.35108% ranking as a ‘Super geek’.)
- Hacker stories.
- See also, of course, Slashdot: ‘News for Nerds. Stuff that Matters’.
- For an excellent introduction to the world of hackers, including interviews and useful background reading, see the US PBS site.





